This article was first published at Inside IT (in German only) as part of Switch's #Security column. The column appears six times a year. Experts from Switch independently express their opinions on topics relating to politics, technology and awareness of cyber security.
Switch DNS Firewall – 'A lot of bang for the buck'
A DNS firewall is an effective and inexpensive protective measure against cyber threats such as phishing and malware. It intervenes at a crucial point – namely where a cyberattack begins. But how do you decide what the firewall should and should not block?

There are truly more encouraging activities than reading the news about cybercrime. The number of attacks in the malware and phishing categories has been going through the roof for a few years now. It is impressive when you consider the absolute figures: In the case of phishing, for example, around 3 billion phishing e-mails and 500 million dedicated phishing attacks per day were already estimated in 2021. Unfortunately, there is no consolation when you put this in relation to the approximately 5 billion Internet users worldwide. At the same time, the attackers only have to succeed once, while the defence measures on a technical and human level only have to fail once for the latter to be successful. This has become more likely with the increasing use of generative AI by attackers. This can have serious consequences under certain circumstances. For example, in an estimated 40 per cent of ransomware cases, a phishing attack is the initial gateway.
Getting to the root of the problem
On a lighter note: Fortunately, we are anything but defenceless. Today, I want to introduce you to one of the many defence measures against phishing and malware. Clear the stage for the Response Policy Zones a.k.a. DNS firewall!
As you can easily tell from the name, this is a defence measure at DNS level. Considering that many malware and phishing attacks start with DNS resolution, it makes sense to intervene at this point – and this is precisely the case with the DNS firewall.
Simple mechanism, great effect
The mechanism is simple and is based on a filter at DNS resolver level. A resolver is responsible for DNS resolution, i.e. a PC or machine requests a resolver in order to obtain the IP address for a domain name. This happens immediately after clicking on a malware or phishing link, for example. In order to achieve a protective effect, a list of known malicious domain names and/or IP addresses is stored on the resolver. Requested domains or resolved IPs are now compared with the list. If the resource is in the list, the resolver can return the IP address of a secure landing page instead of the actual response, i.e. falsify the DNS response to protect the user. This process is shown on the left-hand side of Figure 1. The whole process has no significant negative impact on the response speed of the resolver. Technically speaking, these lists are special DNS zones, the aforementioned response policy zones, or RPZs for short. At this point, I have to admit that I 'borrowed' the second part of the title – 'a lot of bang for the buck' – from one of the originators of RPZ, Paul Vixie. In my defence: I really do think it's an extremely apt quote, as it describes in short and concise words that a DNS firewall is a simple and comparatively inexpensive protective measure.
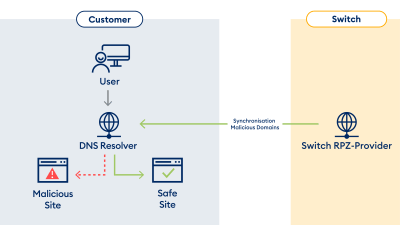
While private individuals generally use their ISP's resolver, many companies and public institutions such as universities operate their own resolvers. In order to achieve a comprehensive level of protection, external RPZ providers are often used, such as Switch. The RPZs are then obtained from this provider via zone transfer, as shown on the right-hand side of Figure 1. With RPZ, however, it is also possible to integrate several RPZs at the same time, which are then connected in series. The protective effect is always additive.
Lots of threat data, keep it coming
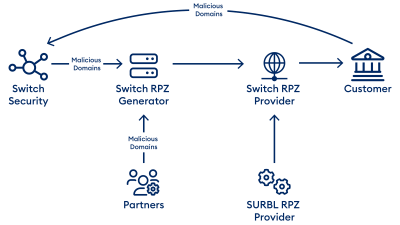
Logically, it is very important for effective protection without overblocking what is in these RPZs and filling them is the real challenge for RPZ providers. As an RPZ provider, Switch collates a wide variety of threat feeds from different regions and providers, supplemented by RPZs from SURBL. This is supplemented by internal data from Switch CERT and IOCs (Indicators of Compromise) reported to us by customers. We process our internal data and the data from the threat feeds and package it in our RPZs. This entire combination is shown in Figure 2. As a general rule, since many attacks are over very quickly or new attacks are added, the RPZs must be regularly updated and distributed.
The quality of the data sources is decisive
The selection of data sources with high quality, i.e. a low false positive rate, is absolutely crucial. Continuous quality monitoring is also very important during operation in order to be able to react quickly if the quality of a data source deteriorates. But even if you pay attention to everything, the devil is in the detail: If URLs are delivered, for example, it may be that only the URL itself is malicious, but the domain within it is not. In other words, a false positive in the DNS firewall context, i.e. at domain level, may not be a false positive from the feed provider's point of view if the specific resource is malicious.
Learning from logs
If we look at the logs of the blocked resources, we can derive further important findings and even actions. An example: Switch receives the RPZ logs from customers and analyses this data. First of all, Switch learns very quickly through corresponding alerts if certain domains are frequently blocked. Either a phishing or malware campaign is then under way, or it is a false positive. In the latter case, we can react quickly and unblock the domain.
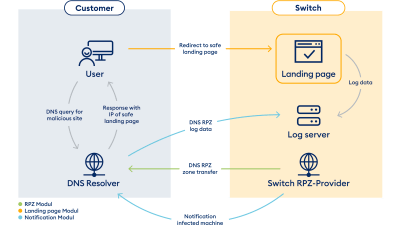
Switch also uses the logs to find out which data sources are the most "valuable", i.e. which are responsible for the most RPZ hits. Last but not least, Switch can assign certain domains to specific malware families with the help of metadata from threat providers or its own knowledge. As a brief explanation: If a device is infected, the malware may attempt to contact specific domains in order to receive commands or extract data. As shown in Figure 3, this is firstly prevented by the DNS firewall and at the same time it is possible to find infected devices if the malicious domains are known. Such hits are then reported back to the customers so that they can find the infected devices and rectify the infection.
A DNS firewall is part of modern cyber security
DNS firewalls offer effective protection against cyber threats such as malware and phishing with comparatively little effort. The use at DNS level enables very early intervention. The quality and timeliness of the underlying data sources are crucial for success. In addition, RPZ logs can be used to gain further insights into ongoing attacks and identify infected devices. DNS firewalls are therefore an indispensable component of a modern IT security strategy.
Link
Discover the Switch DNS Firewall
Cyber Security





