Cyberattack on a hospital – between IT security and law enforcement
A normal morning at a hospital takes a dramatic turn as a cyberattack puts patients’ lives in danger. While CERT focuses on returning to normal operations, law enforcement is trying to catch the perpetrators. A race against time which shows the key factors in the fight against cybercrime.

The sun rises over the hospital in the state-of-the-art city of ‘Digicity’ in Switzerland. The nursing staff are preparing for the change of shift, but when a nurse checks the medication dosage, he notices discrepancies. The prescribed dose of morphine would kill his patient. He quickly realises that it is not the only patient record that has been manipulated. Alarmed, he calls the hospital’s IT department for help.
The attack
The IT department quickly realises that their hospital has fallen victim to a cyberattack. Its own resources have been completely exhausted, but the hospital needs to keep on operating – an IT failure or incorrect data can cost lives. The Head of IT alerts ‘Digicity’s’ Computer Emergency Response Team (CERT). IT security expert Mira Sommer and her team arrive on site in no time. Her goal is to understand the attack, implement protective measures and restore normal operation with data intact. They fight cybercrime by thwarting attackers’ plans and making organisations more secure against future attacks.
It is clear that the attackers have violated Swiss criminal law – they have entered a system without authorisation (Art. 143 Swiss Criminal Code) and have manipulated data (Art. 144 Swiss Criminal Code). It is still unclear whether data theft has taken place (Art. 143 Swiss Criminal Code), extortion is to come (Art. 181 Swiss Criminal Code) and the victim will be coerced into paying a ransom (Art. 155 Swiss Criminal Code).
The dilemma
Mira advises pressing charges. The Head of IT is reluctant: ‘Do we even have to report this? What’s the point? They can’t help! Don’t the police and the public prosecutors have enough to do? Don’t we have to deal with cyberattacks ourselves anyway?’ She mentions an earlier case in which the cooperation with the police and the public prosecutors was not successful and the attackers were not seriously prosecuted.
Please note: The case described and the names and persons appearing in it are fictitious. However, the article is based on real events that have actually taken place in different institutions. The account is intended solely to illustrate the cooperation between a Computer Emergency Response Team and law enforcement.
Mira reminds the Head of IT that while her top priority is tackling the cyberattack, without the prompt involvement of law enforcement, the perpetrators remain unpunished – creating a lawless digital sphere that encourages further attacks.
Mira knows the right contacts. She calls police officer Leo Winter, an experienced cyber investigator who has already been able to put a stop to several international gangs. Both have the same goal of improving digital security in ‘Digicity’, but their functions are fundamentally different.
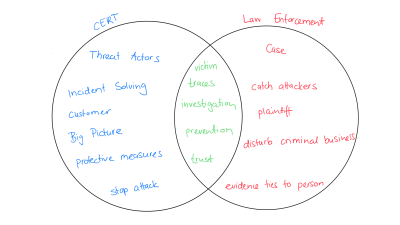
- Mira wants to assess traces the attackers have left behind, take protective measures, stop the attack and return to normal operation with as little damage as possible.
- Leo is responsible for public safety, law and order. In this case, he wants to investigate the perpetrators and needs usable evidence.
The sooner he receives relevant information, the sooner he can investigate, but if the data is too old, it becomes almost impossible to prosecute the perpetrators.
Both do their jobs, but they can only have a lasting impact on digital security if they work hand in hand.
Challenges of the cooperation
| Perspective of CERT | Perspective of law enforcement |
| Mira is interested in the traces the attackers have left behind in order to get an overall picture of the attack. This enables her to take helpful measures to protect the hospital and its partner organisations. Information about the perpetrators as individuals is of little use to her in her work. | The technical information from Mira puts Leo on the right track. He must be able to match the information from the case to one or more specific persons in order to prosecute them. |
| In terms of resources, Mira has to make sure that her work is cost-effective. Her commitment to the common good of ‘Digicity’ and the profitability of her work – something which is a constant balancing act – determines how much of her time and knowledge she dedicates to helping Leo’s investigations. Unlike Leo, however, Mira is able to adapt much more quickly to current threats and the specialist field with the available financial resources and lean structures. | Leo is working under enormous pressure as cybercrime continues to increase. Although digitalisation brings many benefits, it is not only shifting life and work to the digital sphere, but also crime. Keyword: Cybercrime-as-a-Service. Leo’s resources, both human and professional, are limited. Any specialists the police have are quickly poached, meaning the police and public prosecutors can barely keep up with the development of new threats and the professionalisation of cybercrime. |
| In terms of legal options, Mira has more freedom than Leo, as a CERT is less subject to legal restrictions than a public authority. This means that she can use any technical solution which is not prohibited by law in her work. Nevertheless, Mira needs to be aware of her own criminal liability, so that she doesn’t break the law just because something is technically possible. It’s a difficult balancing act. | Leo, on the other hand, is bound by strict legal conditions. He is often unable to act to the extent necessary for his work and the law often lags behind the types of crime in the digital sphere. This results in constant tension where he has to carefully weigh up his actions against the legal possibilities. He can only do what is expressly permitted in law enforcement. |
| The political system is also a challenge for both. Mira is more focussed on societal values and, thanks to her flexible working environment, has more leeway at a national and international level to respond to current threats. Mira feels very comfortable operating in a fastpaced and agile environment and this makes her work easier. | Leo is strictly bound to the federalist system, which makes cooperation between different authorities difficult. This is particularly problematic when it comes to combating cybercrime, as it does not respect territorial boundaries. In this type of system, efficient cooperation is challenging. |
| Ensuring cooperation and trust are maintained between Mira and Leo is also not always easy, as Mira often has to set her own limits and focus on her primary mission. This can lead to tension when Leo is expecting support. She is only allowed to know to a limited extent whether and to what degree the information and assistance she provides are of use to Leo’s investigation during an ongoing case – something which she finds frustrating. | Leo, on the other hand, relies on the help of Mira and other partners. However, cooperation is often hampered by legal restrictions. Both sides often don’t know how their work actually helps the other person – this creates a ‘black box’ situation. It requires a great deal of trust, tact and pragmatism. You can gain a lot from working together, but you can lose just as much. |
Shared success
Both parties – Mira and Leo – share the same goal of achieving long-term digital security. They both now understand their complementary role and are therefore able to successfully solve cases.
The current goal is to ensure the security of the hospital in ‘Digicity’. Despite the huge number of obstacles, Mira and Leo find a solution. The attackers wanted to cause chaos, they manipulated data and stole the correct data. They are demanding a ransom. Mira tracks down the source of the attack, while Leo activates his contacts. The gang is caught abroad and summary proceedings for international legal assistance allow data to be retrieved – and all this within 48 hours! With the right data, Mira can manage the IT security incident and return the hospital to normal operation. Leo has caught his culprits and can use Mira’s information to present an unbroken chain of evidence of the crime. Without each other, this would never have been possible
The core of the matter
Transparency, mutual understanding and coordinated cooperation are essential to effectively combat cybercrime – now and in the future.
About the author
When Darja-Anna isn’t hyperfocussed and trying to solve a puzzle with digital forensics, she talks to people and tries to pass on her enthusiasm for IT security. She also manages computer security incidents and enjoys collecting every new piece of the puzzle. She has been passionately been doing this for Switch CERT since 2020.






