This article was first published at inside-it.ch (in German only) as part of Switch's #Security column. The column appears six times a year. Experts from Switch independently express their opinions on topics relating to politics, technology and awareness of IT security.
With passkeys into a passwordless future
Phishing attacks, along with fraud, are among the most frequent cyber incidents in Switzerland. Passkeys pave the way to a phishing-proof and user-friendly future without passwords. This is how it works.
Phishing attacks are ubiquitous. Cyber criminals steal and misuse sensitive data such as credit card numbers or access information. Besides the shameful and unpleasant feeling when cyber criminals take over one's own user account, this also leads to enormous economic damage. Cyberattacks have increased sharply in Switzerland in recent years and cause billions of dollars in damage worldwide. Adequate protection against cyberattacks has therefore become indispensable for every company.
Key measures for ensuring cyber security include protecting user accounts and raising employee awareness. A single compromised account can be enough to cause lasting damage to a company and paralyse systems.
Two-factor authentication as a key element of cyber security
User accounts thus often play a central role in cyberattacks. Be it for the direct exploitation of authorisations in systems or indirectly for the collection of internal company information. Unique and complex passwords contribute significantly to increasing account security. In combination with two-factor authentication (2FA), which requires an additional identification factor, users can already realise increased protection against unauthorised access. Studies clearly show that the use of multiple factors for authentication significantly reduces the risk of compromise compared to the exclusive use of a password.
In general, however, two-factor authentication via SMS or authenticator app is unpopular, time-consuming and can more easily lead to users being locked out of their accounts if their smartphone is lost. For these reasons, two-factor authentication is made as easy as possible, which unfortunately often comes with a reduction in account security. In addition, common two-factor authentication methods are not protected against phishing attacks, meaning cybercriminals can intercept the credentials and misuse them for unauthorised access. A more secure and user-friendly alternative to traditional account security would therefore counteract the classic trade-off between security and ease of use.
Passkeys: No more compromises
In contrast to conventional passwords, passkeys work with a cryptographic public key procedure. They thus follow a fundamentally different approach. Instead of passwords, passkeys use an asymmetric key pair. This consists of a public and a private key, whereby the private key is securely stored on the end devices of the users. This approach mitigates the risks associated with password-based authentication. The storage of passwords is replaced by the possession of the private key on a secure device.
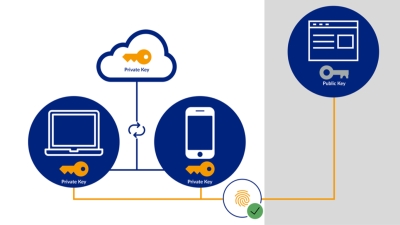
Properly configured, passkeys enable two-factor authentication. In addition to possession of the passkey (1st factor), explicit identification (2nd factor) can be requested. Users are prompted to use a passkey with fingerprint, facial recognition or PIN support for corresponding services. This is usually done using a notebook, smartphone or a hardware-based USB authenticator.
Passkey's underlying technology, the WebAuthn standard, has been around for several years. Recently, however, significant progress has been made in standardisation. In particular, all major browser and operating system manufacturers have joined forces in the FIDO Alliance and are striving to integrate the technology into their solutions. This alliance not only creates a comprehensive security standard, but also ensures strong interoperability and thus improved usability. In this context, the term Passkey was coined to describe the new technology.
Cloud synchronisation of passkeys
As shown in the graphic above, the private key required for authentication can be synchronised on all end devices of the same cloud account (e.g. Google or Apple) via cloud synchronisation and end-to-end encryption. By registering a passkey on one end device, it usually automatically becomes available on all end devices of the cloud account. As long as users have access to the cloud accounts, this also secures recovery procedures, for example in the event of a smartphone being lost. As described, it is also possible to register passkeys without cloud synchronisation, e.g. with a USB authenticator. Ultimately, it requires an individual assessment in which cases cloud synchronisation meets the compliance requirements. For private individuals, this assessment will look different than for companies.
Logging in to a previously registered service is then very easy with the help of a passkey.

Users access a service, enter their login name and are then asked for biometric proof or a PIN. So passkeys do indeed solve many authentication hurdles one is confronted with in the daily online world. Three essential points should be highlighted again:
- Better user friendliness
The user experience becomes familiar and uniformly standardised across many devices on different platforms. So passkeys make it easy to navigate the web with confidence. - Enhanced security
Passkeys are based on cryptographic technologies that have proven resistant to phishing and other attacks. This allows account security to be significantly increased without any additional effort. - Scalability
With Passkeys, the inventory of passwords can be reduced and limited to a single trusted store that manages all cryptographic keys for the user. Gone are the days of password notebooks.
The technology thus has the potential to permanently change and simplify the way we authenticate ourselves on the web.
Browser support under construction
It should also be said, however, that all that glitters is not yet gold. Many browsers and operating systems have already supported the standard for several months, and so passkeys can be registered on current Apple and Android devices. Unfortunately, there are still common browser and operating system combinations that do not yet fully support the standard. Firefox, for example, currently has limited support for the standard required for passkeys. These restrictions still affect the early-birds. However, the problems will gradually disappear.
Full of curiosity into a passwordless future
In today's world, adequate protection of sensitive data is essential. Strong passwords provide basic protection against cybercriminals, and when combined with a second factor, account security can be significantly enhanced. Traditional two-factor authentication with SMS or authenticator apps remains cumbersome and not fully resistant to phishing attacks.
With Passkeys, a new authentication method is establishing itself that overcomes the usual compromise between security and user-friendliness and offers a passwordless, phishing-proof alternative to passwords. SWITCH edu-ID, the digital identity of Swiss university staff, has implemented this function in recent months and is currently gathering initial productive experience with selected users. It will probably be a while yet before passkeys are fully established in our everyday lives, but the secure future in the field of authentication on the internet is certain.
Digital Identity
Cyber Security





